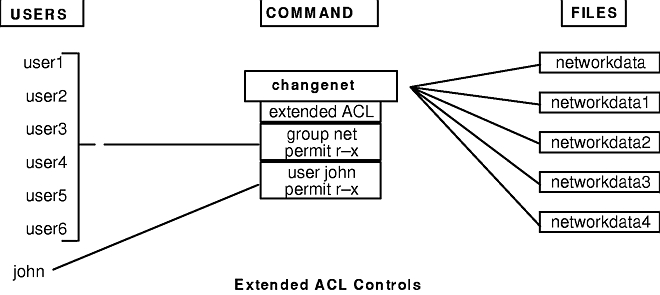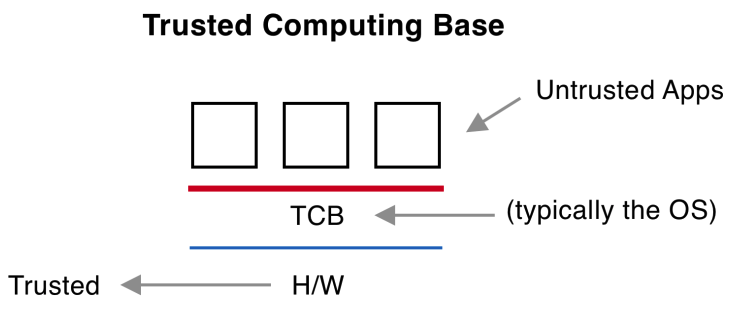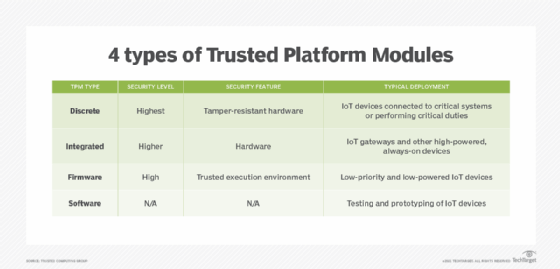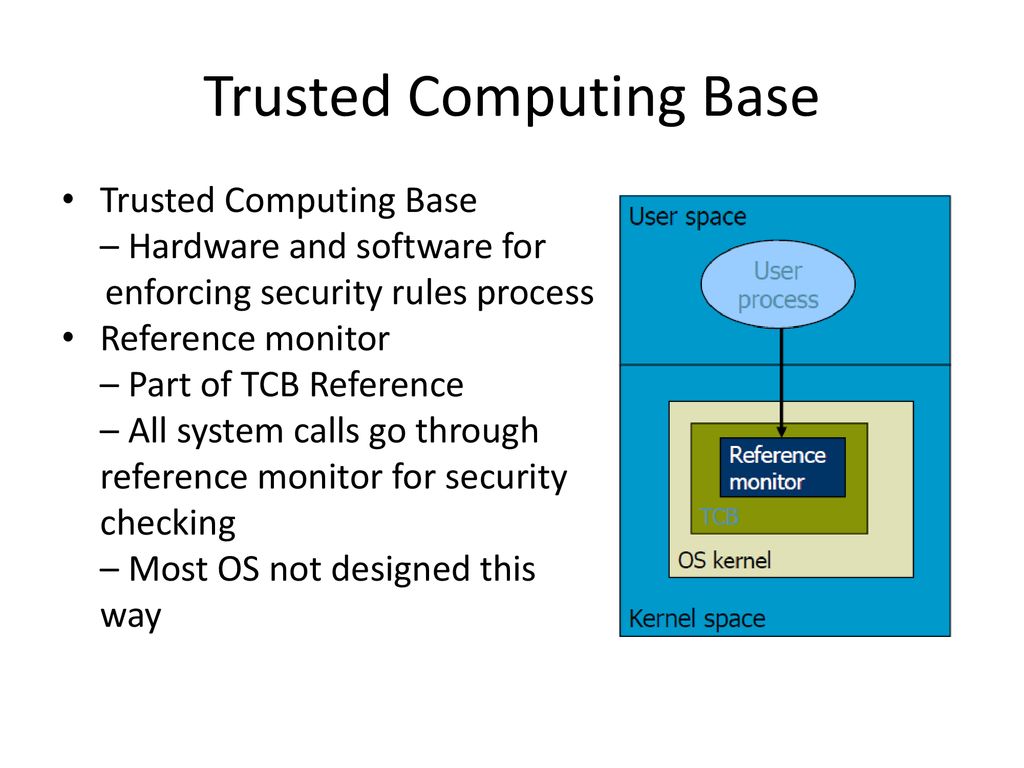
CISSP PRACTICE QUESTIONS – 20190822 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

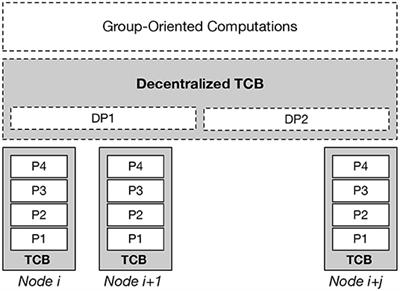
European Centre for IT-Security ( eurobits ) 1 European Multilateral Secure Computing Base Open Trusted Computing for You and | Semantic Scholar

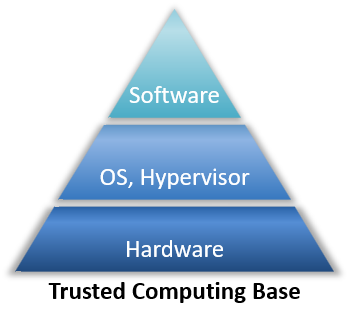
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification

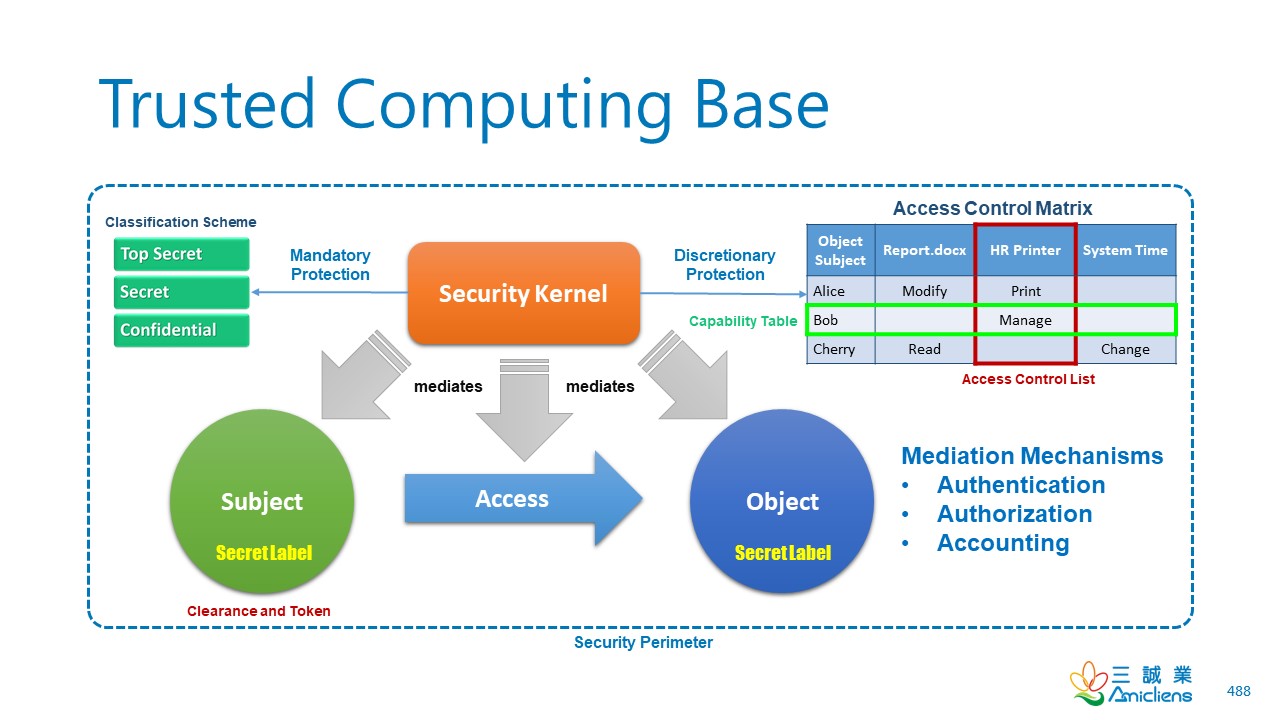
______ is the boundary that separates the trusted computing base from the remainder of the system. - Skillset
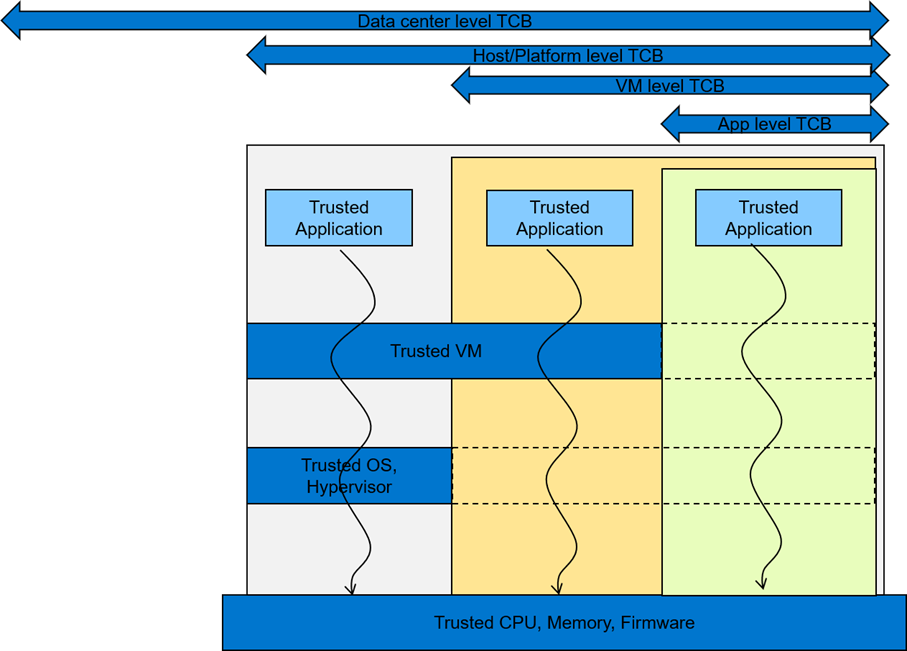
Understanding Confidential Computing with Trusted Execution Environments and Trusted Computing Base models | Dell Technologies Info Hub