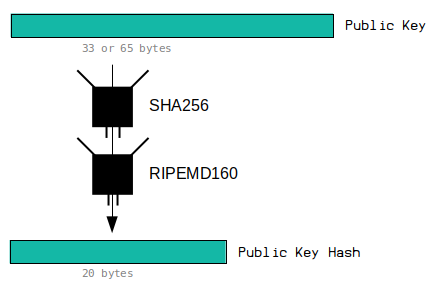
Security Hardware Accelerator #6 SHA256 in hardware acceleration - Blog - Summer of FPGA - element14 Community
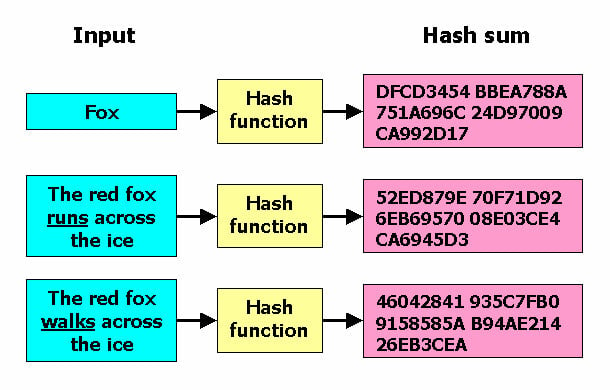
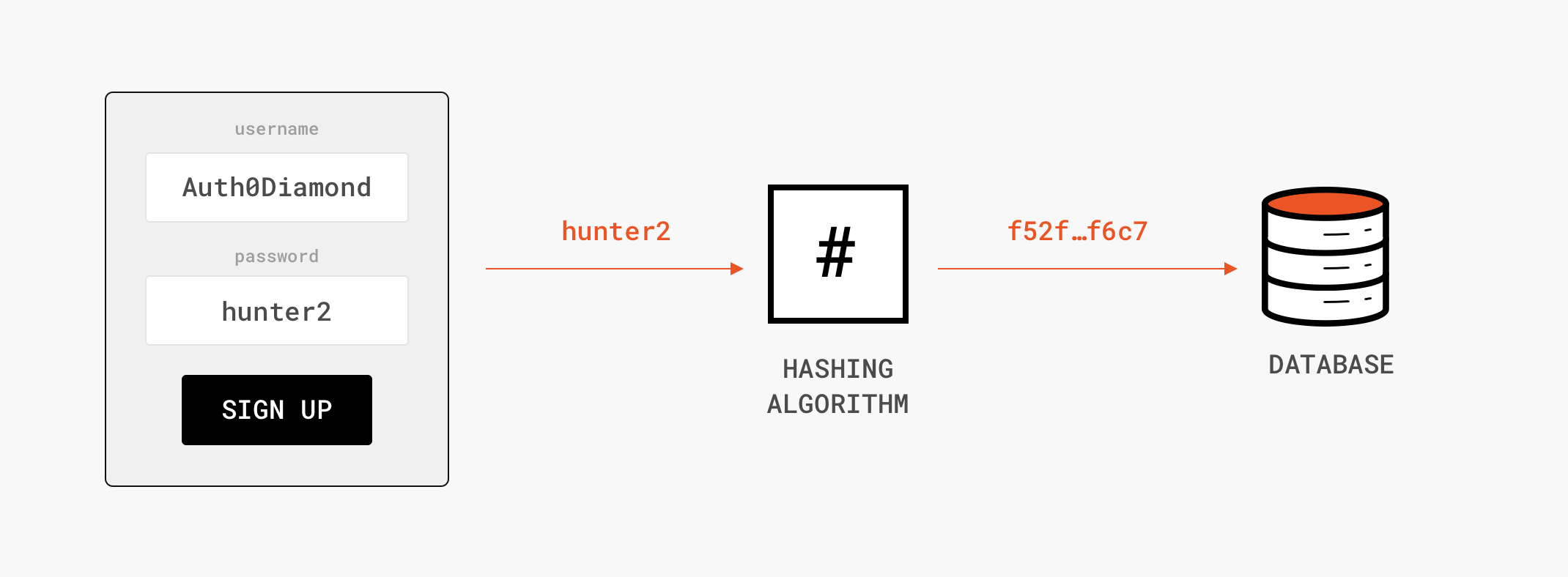
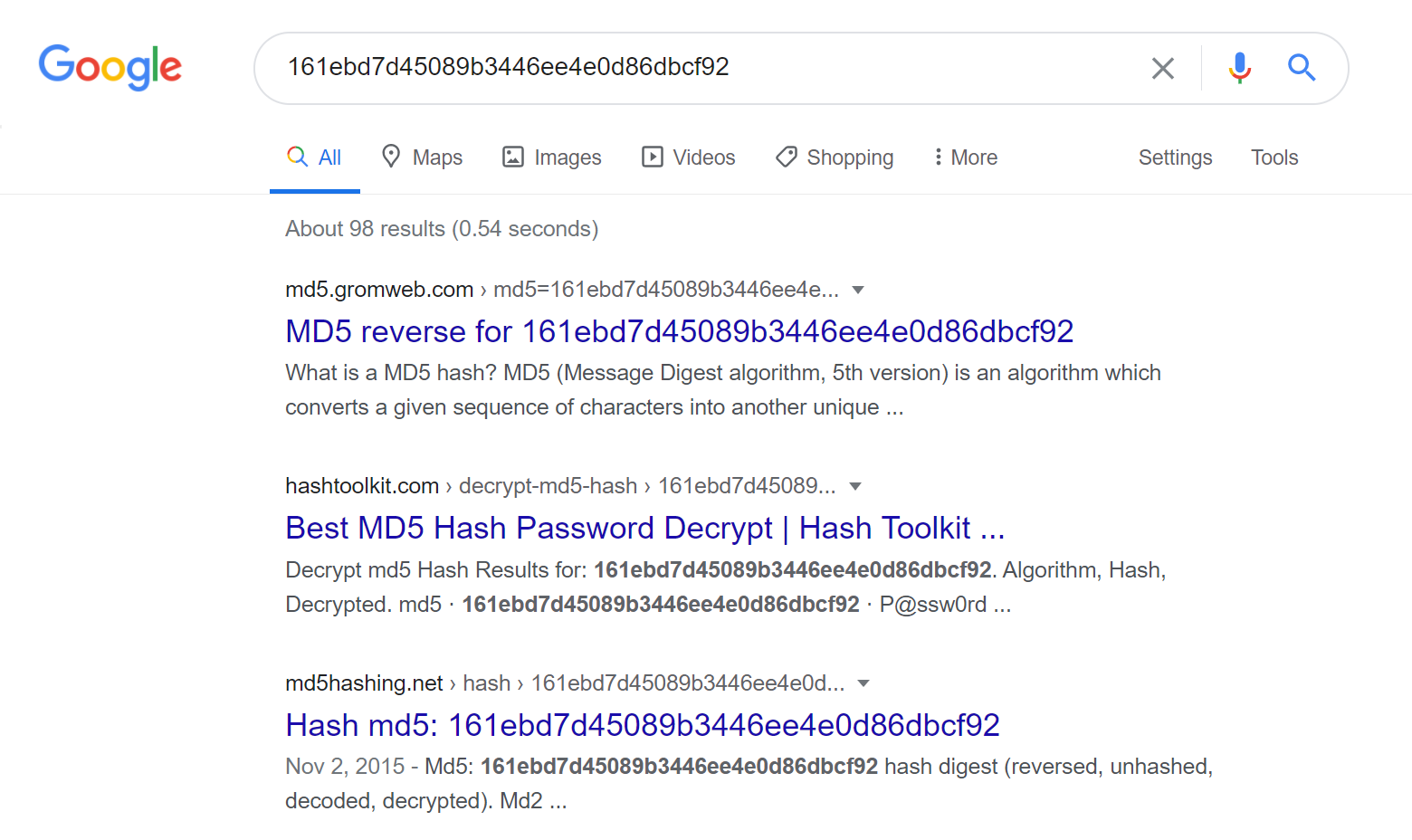
Why is the SHA-256 hash function impossible to reverse? I saw the mathematics of 'how to manually convert a text to SHA-256' here: https://qvault.io/cryptography/how-sha-2-works-step-by-step-sha-256/ Can't we just go backwards? - Quora